What is Regin
Introduction
Regin is a Trojan malware that steals user’s data by redirecting them to the spoofed web pages. In 2010, Belgacom the Belgian telecommunications company was hacked, and this attack was discovered in September 2013, but at the end of 2014, it’s given the name of Regin. The attack was the work of Western Intelligence, especially. GCHQ, the report by Edward Snowden. The complete operation named by Operation Socialist. It was found that Belgacom employees' internet connections were forwarded to a phoney LinkedIn page, which was used to infect their computers with malware known as "implants" by GCHQ. Regin was the highly complex malware that has been used during Operation Socialist.
What is Regin Trojan horse Malware?
The Regin Trojan horse malware is cyber-attack platform that uses GSM networks to get into their spying motives. Regin deploy in the victim networks for ultimate remote control at all possible levels. With a platform that is extremely modular in nature, it has multiple stages to finish various parts of the attack.
Regin also known as Prax or QWERTY. Regin malware majorly used by United States National Security Agency (NSA) and its British Counterpart, the Govt. Communication Headquarters (GCHQ). Regin was first publicly revealed by Kaspersky Lab, Symantec, and The Intercept in November 2014.
How Regin Trojan Malware Works
Regin is a modular framework when the attackers can enable or disabled certain elements and load specific code, called a “payload,” to create a Regin version that is specifically suited to a specific mission. Remember that it’s not confirmed yet, whether all the payloads have been discovered, and that there may be more than the ones specified here.
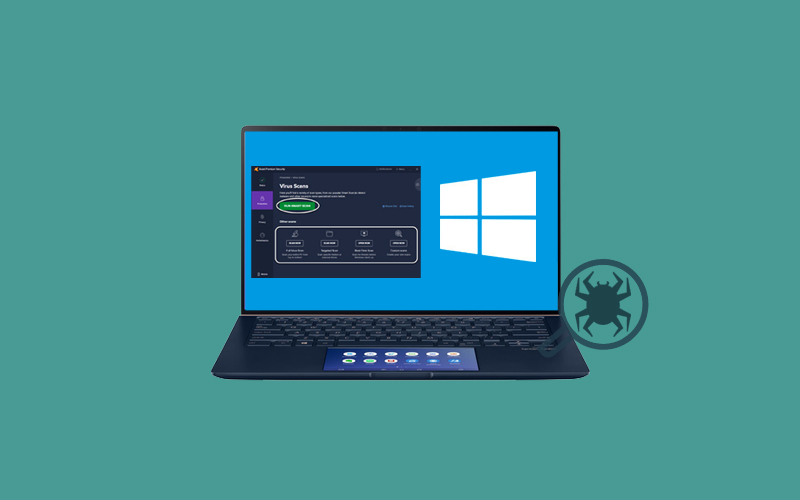
Regin has six stages in its architecture
In the Symantec analysis, Regin's design is divided into six stages, which are referred to as Stages 0 to Stage 5.
Stage 0
The virus is first installed on the target's computer by a dropper trojan horse.
Stage 1 and 2
Once installed virus on the system, then it will loads multiple drivers as well as compression, encryption, and networking.
Stage 3 and 4
Loads the encrypted file container (EVFS) and also loads some additional kernel driver, plus the payloads
Stage 5
In the final stage, it loads the main payload and the necessary files for it to operate.
Regin malware first of all targets against Microsoft Windows Operating system computer, as all of the files discussed in the Symantec report are highly Windows-specific. But there may be payloads out there that also target GNU/Linux or OS X computers.
It yet not cleared the extent of Regin malware. But, it contains strong capabilities to infect Windows computers. Regin was significantly founded in 2010, the very first time, but some components of Regin were traced back all the way to 2003.
Note: The name Regin is first found on the VirusTotal website on 9 March 2011
Risk of State-Sponsored Malware and Its Target
Regin is a highly advanced spying tool used in cyber espionage campaigns against individuals, governments, private corporates, researchers, and infrastructure operators worldwide. Regin is considered much more than a highly sophisticated malicious code; experts consider it a complex modular hacking platform.
It was reported that Regin has a degree of technical competence rarely seen. Security experts speculate that it has some resemblance to other state-sponsored malware like Flame, Duqu, and the popular Stuxnet.
Symantec reported in its analysis that the development of Regin required a significant effort, time, money, and many experts immediately accused a Western intelligence agency of a massive espionage campaign. We will also see that there are also other illustrious opinions on the case; a part of the security community considers that it is not possible to exclude in this phase that Regin is the product of cybercrime.
As we already know that Regin attack platform is a technology designed by U.S. and British intelligence agencies, according to security industry sources and technical analyses conducted by The Intercept itself.
The danger of this state-sponsored malware may very well prompt the companies, individuals or states that the malware surveillance is targeted against to take countermeasures, leading to a digital arms race. This may be subsequently lead to war, especially when a nation’s critical infrastructure is targeted. But, Regin does not end here, it can spread more threats and risks for multiple targets.
Regin only compromised security, but also danger for life. Security gets compromised when bugs are left unsolved and back doors built in to let the spies in and let malware do its work.
It also impacts Government security. Government backdoor and malware is not guaranteed to be used only by the government. Others can get a hold of the malware as well, and security vulnerabilities can be used by other than just spies, for example, stealing credit card details.
Regin-Target Profiles
As already explained, the Regin has multiple targets across several industries, including:
- Government institutions
- Multi-national political bodies
- Telecom operators
- Financial institutions
- Research institutions and individuals involved in advanced mathematical/cryptographical research (e.g. popular Belgian cryptographer Jean Jacques Quisquater).
Kaspersky Lab researcher says the identification of the infected machines is advantaged by the fact that even after Regin is removed, certain artifacts and infection markers are still present in the systems. The Kaspersky Lab team has identified the infection in 14 countries.
- Algeria
- Afghanistan
- Belgium
- Brazil
- Fiji
- Germany
- Iran
- India
- Indonesia
- Kiribati
- Malaysia
- Pakistan
- Russia
- Syria
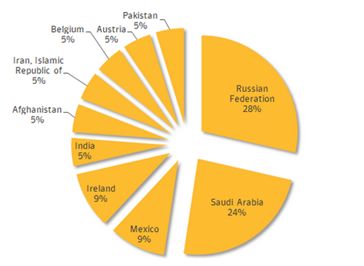
Symantec report highlighted the infection of Regin attacks was prevalently observed in ten different countries. The number of infections is prevalent in the Russian Federation, Saudi, Ireland, and Mexico.
Graphical data representation
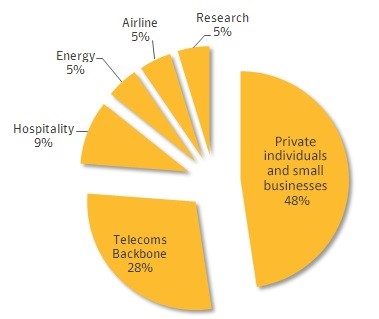
It is stated that the distribution of targeted industries reveals that Regin was used to compromised Telecom Backbone in 28 percent of the attacks and that in 48 percent of attacks; the victims were private individuals and small businesses. The experts also believe that the operators managing the cyber espionage campaign were interested in spying on the specific customers of the targeted companies.
Graphical data representation
Is it possible to smite Regin?
With the help of this guide, you would probably have known till now that Regin is more than a complex malware and even after uninstalled, the Regin impact is still disturbing. However, prevention never should end from the user’s end. For example, Regin mostly targeted Windows Operating system computers, and as per the research, it’s so common that most of the users don’t follow the basic security measures on Windows system, except the default one.
History says, outdated and old version computer operating systems, applications are always more vulnerable to attacks than the updates and new version. However, we have to follow these procedures on our own, but now technology made it easier. There are various anti-malware and Updrivers tools are available that make this takes completely hand-free. We recommend you to use Waredot Total Protection that keeps your computer updated, provides protection against all types of malicious software.
This software contains over 15 million malware’s signatures and advanced module of proactive protection for every version of malware.
Conclusion
Hey guys! This was the guide about “What is Regin.” Threats are always going on, and it is always advised to be more cautious, warning that “on the Internet, attribution can very easily fail and false flag operations are quite common,” by Costin Raiu.
You will daily encounter spoof web pages, malicious links, default installing malicious software, etc. that will cause malware on the system. Additionally, investigation about Regin is still going on, as it’s crucial to have more knowledge about Regin malware.