How to Remove THANATOS- A Ransomware
THANATOS ransomware was the first program to accept ransom in payment in Bitcoin Cash.
THANATOS is ransomware first uncovered by MalwareHunterTeam 2018. This ransomware perfectly designed for data theft or loss in order to get the ransom from the victim. However, there is no guaranty that after paying the ransom; the victim gets their data.
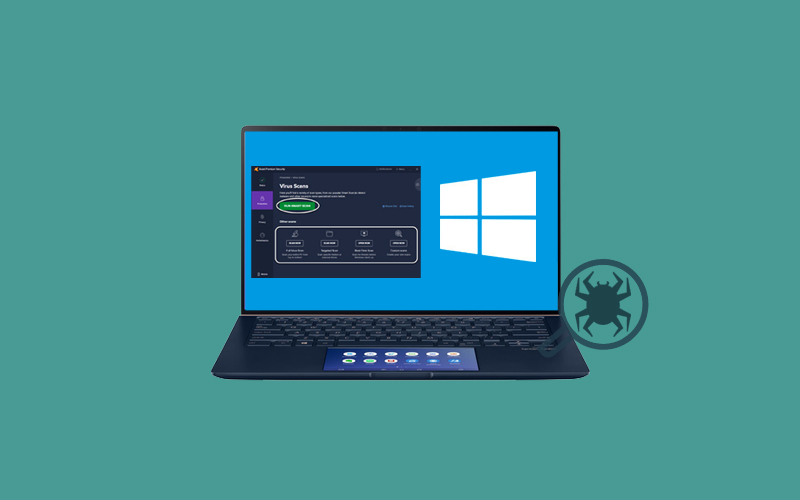
THANATOS ransomware encrypts your most stored file and ad the ".THANATOS" extension to the name of each compromised file. Once your files are encrypted, you cannot use them. After successfully encrypting files, THANATOS places a text file ("README.txt") on the desktop. This README.TXT will pop up every time the user reboots the system because of the autorun registry dropped by the malware. We will show you how the message looks like.
Tip:
In Greek mythology, Thanatos is a figure who represents death. In psychoanalysis, Thanatos is a person's urge toward death or self-harm.
How THANATOS Ransom Executed?
THANATOS ransomware encrypts most stored files and appends the ".THANATOS" extension to each compromised file's name. For instance, "sample.jpg" becomes "sample.jpg.THANATOS." Once files have been encrypted, they are no longer usable. THANATOS creates a text file ("README.txt") on the desktop after successfully encrypting files.
Now, you will see that a new text file will appear with a short message claiming that the system is infected and that the victim must pay a ransom to restore files. The decryption of these files requires a key generated for each victim. However, these keys are kept on a remote server that is under the control of cybercriminals (developers of THANATOS). A ransom must be paid by the victims. 1 Bitcoin (now worth $1130) for the release of their keys, which they are intended to receive by email at the address provided. However, cybercriminals are not meant to be trusted. Therefore, we recommend you to ignore all requests to submit payments. You will lose your money and support cyber criminals’ malicious business.
Note: THANATOS does not specify whether it uses symmetric or asymmetric cryptography, hence this information is currently unavailable.
How THANATOS Ransomware Spread
THANATOS ransomware spreads in a number of ways on your pc and you might not get what is going on with your device. It just that everything has one source to come in the room either from the front door or back door. A cyber-criminal always uses backdoors to come into the house rather than the front door, as it’s easier to enter from the backdoor. Let’s look at a few of the major reasons that let’s enter the THANATOS ransomware on your system.
- Infected email attachments (macros),
- Torrent websites
- Malicious ads
- Interactions with already infected PC with THANATOS
- Drive-By Downloads From a Compromised Website
- Through Wi-Fi network
- Remote Desktop Protocol
- USB and Removable Media
Tip:
As research says, THANATOS ransomware takes the average time to start encrypting files on your PC or network is only 3 seconds.
How to Protect Yourself from THANATOS Ransomware
Protecting yourself from the THANATOS virus does not include a one-way solution. You need to be very strict for each and every activity you perform on your device and try to gather the information about all the phishing emails and what most common point in all of this. Enhance your knowledge so that you’ll be able to judge any phishing emails or fraud, website, and a lot more.
Note: Unfortunately, there are currently no tools capable of decrypting data compromised by THANATOS and you can only restore everything from a backup.
However, this can’t be enough to secure your device. You should also run an antivirus on your device. You can use 3-Scan Mode Waredot Antivirus that helps you to secure your device from viruses, malware, ransomware and etc.
Waredot antivirus offers filtration of every incoming and outgoing email to protect the device from any suspicious threats. So, it will secure your device from phishing emails which is most common reason for ransomware attacks.
Waredot antivirus also works out of the box. It means, whenever you connect your device with another one through a USB drive, Waredot antivirus detects and analyzes and displays information regarding the disk security to the user. If the program finds something suspicious, it prompts the user immediately.
Download Link: Waredot Antivirus
Countermeasures and Best practices for prevention:
- To reduce the risk of data loss, make regular backups of all vital information.
- Maintain the most recent patches for the operating system and third-party apps (MS Office, browsers, browser Plugins, and antivirus).
- When surfing the internet, use caution. Ascertain that the web browsers are sufficiently secure, with suitable content controls.
- When using MS Office, always disable macros and Active X.
- Never open attachments sent from unknown email addresses. Delete these emails without reading them right away.
- It is strongly recommended that you only download apps from official sites and use direct download links.
- Third-party downloaders/installers are commonly used to spread rogue programmes, making their use extremely dangerous.
- Make sure your system, applications should be up-to-date. If you don't remember updating your program, use Waredot Updrivers that automatically updates your pc, applications and also do quick scanning with zero compromise.
- Make sure to always take a routine backup of your important data in external driver like HDD and pen drives. You can use reliable Cloud service to store the data.
- Do not install any freeware or cracked versions of any software.
- Do not open any advertisement pages shown on websites without knowing that they are genuine.
Conclusion
Hey guys! This was the guide about “how to remove THANATOS- A Ransomware.” However, we’ve discussed in this article that removing the THANATOS virus is not possible. There are no solutions found yet that could help you to decrypt the encrypted files on pc. Still, we have listed some pre-maintain activity that you should follow and always run an antivirus program on your device. We recommend you practice the above measures till then we can’t get the solution to decrypt the files for free.
Hope you find this article helpful and informative. If you’ve any queries regarding this article, please let us know in the comment section below.