List of Ransomware- 2016
List of ransomware 2016 provides you adequate knowledge on the most dangerous attacks of ransomware in the form of malware, Trojans, viruses, and etc. We’ve listed all the ransomware held in 2016 so that if this ransomware or types of ransomware disturb you anytime, so you’ll have adequate knowledge to deal with them.
These viruses still exist and we found in our research that many businesses compromised with ransomware found in 2016. So, if you’re working or running a professional, then this guide surely help you to resolve or avoid these ransomware. Read on.
1. MEMZ-January 2016
MEMZ is malware in the form of the Trojan horses virus. It was first developed in January 2016 by Leurak, who explained that the Trojan was intended merely as a joke. It was later featured by Joel Johannson, allies Vargskelethor, a member of the live-streaming group Vinesauce on his series Windows Destruction, who demonstrated the Trojan in action against a Windows 10 virtual machine after being provided with a copy by danooct1.

The Trojan alerts the user that it is a trojan and warns that if they continue, the machine may become unusable. It contains sophisticated payloads that corrupt the system, causing artifacts to appear on the screen while the program runs. Once installed, the application cannot be uninstalled without causing further damage to the machine, which will eventually stop working correctly. And once your computer restart, in place of the Bootsplash is a message that reads “Your computer has been trashed by the MEMZ Trojan. Now enjoy the Nyan cat…”, which follows with an animation of the Nyan Cat.
What Does MEMZ Trojan Do?
MEMZ Trojan plays with the users, it uses highly complex and unique payloads and activates them one by one. The first few payloads are not damaging but the final payload is the most harmful since the malware runs a few programs to make changes to the system and make sure persistence. Your PC may become completely unusable.
First of all, MERM primarily corrupts the boot sector of the Windows operating system. It overwrites the first 64 KB of the hard disk, which means that the Master Boot Record is impacted and some advanced troubleshooting tips are necessary.
How to know if your PC is MEMZ Trojan virus-infected
It’s not so difficult to find out whether your pc infected with MEMZ virus or not. When your computer is infected with MEMZ Trojan, notice that some version of the virus will display a message to let you know the file is on the PC before it spreads. However, it may possible that you wouldn’t get to know that actually there is a virus file until you see a Notepad warning saying your computer won’t boot up again.
Additionally, you may notice some activities performing on your pc below, but still we recommend you to do not come at some point without any confirmation. These symptoms may happen due to some other issues.
- Your web browser opens without warning and displays search results for disturbing things
- Mouse cursor moves on its own and error messages appear
- Applications open and close out of nowhere
- Odd errors occur and system crashes
- Many pop-ups appear on the screen along with Internet memes and random pictures
Additionally, it may also cause display colors inverting every second, takes a snap of the screen, and display them in a tunnel effect at growing speeds.
How MEMZ Spread?
Most of the viruses whether it is Trojan, Malware and etc. spreads through phishing emails, software downloads, infected websites, and email attachments. So, we strongly advise you to for all viruses, you should not click on phishing emails, attachments, do not download any software from untrusted websites or sources, do not visit an infected websites and etc.
Additionally, when using free file hosting sites, freeware sites, or peer-to-peer networks like Torrents, your machine may be at a high risk of MEMZ.
How to Remove MEMZ Trojan Virus
Use Waredot Antivirus to check for viruses, malware and threats on your computer and to remove them too. Waredot antivirus protects you from all kinds of viruses, malware, attacks including ransomware and etc. It notifies you whenever there is something suspicious on your system and removes the threats as well. You can run its 3-scan mode for threat scanning and remove them easily. Additionally, update all your outdated program, systems to the latest version.
Make sure to update drivers on your system. Use Waredot Updriver for DIY update. It automatically checks for all the outdated and old version drivers on your system and update them with the latest version. If you install any new driver, Waredot updriver pre-check for installation and approve for branded and official drives only.
Do not click on any suspicious link received via email or text on the phone number. These types of malicious links can add threats on your device or software by default.
Do not download software or anything from an untrusted website or source. Always use the official websites and don’t get trapped in free schemes.
We strongly advise you to use a secure VPN to protect yourself from the risk of malware when using public Wi-Fi.
Make sure to take Backup Data on a routine basis.
Ransomwar Locky- February 2016
Locky is a ransomware virus that was first discovered in 2016. It comes in the form of an email (that seems to be an invoice demanding payment) with a Microsoft Word document attached that contains harmful macros. [1] When the user views the document, it looks to be filled of nonsense, with the text "Enable macro if data encoding is incorrect," which is a social engineering tactic.
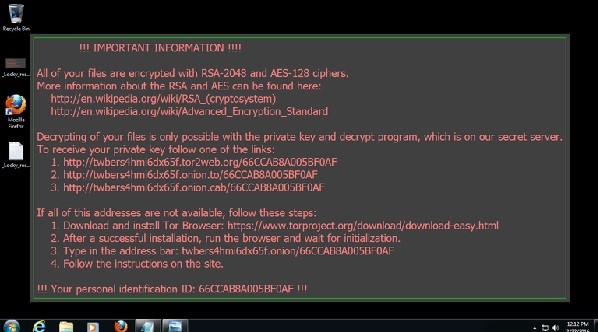
How Does Locky Ransomware Work?
Locky ransomware spread by email, using social engineering techniques to spread the malicious code. Necurs primarily distributed the Locky ransomware and then Dridex banking Trojan in its spam emails. Locky virus will use emails to spread the threat and thus, the mechanism of Locky involves receiving an email with a Microsoft Word document attachment that contains the code. The documents prompt the user to enable the macros to see the documents. Once the virus is deployed, it will get loaded into your computer system’s memory. After that, it will begin encrypting documents, renaming them as hash locky files. In addition, Locky installs.bmp and .txt files, and will encrypt network files that the user has access to.
Locky Prompt You in Email Messages
An example message with Locky as an attachment is the following:
Dear (random name):
Please find attached our invoice for services rendered and additional disbursements in the above-mentioned matter.
Hoping the above to your satisfaction, we remain
Sincerely,
(random name)
(random title)
How Locky Spread?
As per cased research, we found that Locky uses many different distribution methods to spread the virus. These distribution methods include exploit kits, Word and Excel attachments with malicious macros, DOCM attachments, and zipped JS attachments.
2. Tiny Banker Trojan- February 2016
Tiny Banker Trojan can be identified with its name, and it marked since its discovery as it has been found to have infected more than two dozen major banking institutions in the United States, including TD Bank, Chase, HSBC, Wells Fargo, PNC, and Bank of America. Tiny Banker Trojan is also known as Tinba
Tiny Banker is an offshoot of the banking Trojan line of malware which includes the Zeus Trojan from which the name Zusy developed. We found that Tiny Banker Trojan uses HTTP injection to force the user’s computer to believe that it is on the bank’s website. They performed and established as it really comes from the bank. It’s really hard for users to identify it as it works like the real one as well.
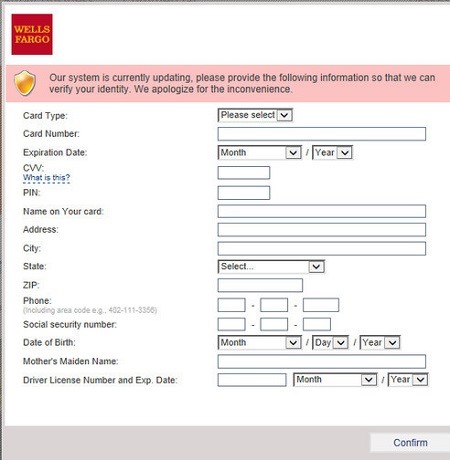
If users couldn’t recognize it, they will enter their information to log on, at which point Tinba can lunch the bank webpage’s “Incorrect login information” return, and redirect the user to the real website. Now, users will think they had entered the wrong information and the user would continue as normal, although now Tinba has captured the credentials and sent them to its host.
This is how Tinba steals your sensitive information without your knowledge. And that’s why sometimes it’s really difficult to recognize the malicious website because they appear and work completely like the real ones.
Indication of Tiny Banker Trojan
Here you can find few indications to detect that you’re infected with the Tinba. However, for most of the user, it’s difficult to detect that their device has been compromised, there are a number of clues to watch for. These clues can also be useful for security professionals managing user systems:
Note: We do not confirm that these clues only confirm that you’re infected with Tiny Banker Trojan. It may be caused due to other reasons.
- Browser that load web pages slowly and run sites slowly.
- Your computer fan is constantly running or a hard drive that is always spinning could be a sign of an infection.
- If you notice any suspicious behavior.
- Unexpected bank notification or new form elements in banking web pages, for example. Filed that ask for credit card number or PINs.
- Failed login attempts the first time you attempt to log in despite the password being entered correctly.
- Unexpected pop-up Windows are often a sign of an infection. Clicking on those pop-ups can install additional malware.
- Anti-virus solution that stops working.
3. Mirai- September 2016
Mirai is malware that first discovered in 2016 September that infects smart devices running on ARC processors, and turning them into a network of remotely controlled bots or “zombies.” This network of bots known as botnet is often used to launch DDoS attacks.
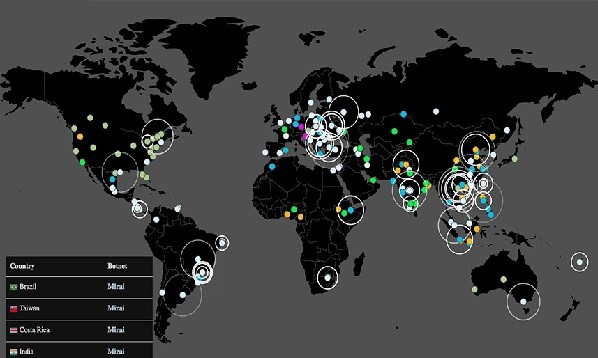
The creators of the Mirai Malware launched a DDoS attack on the website of a well-known security expert. And after a time, they released the source code into the world, possibly in an attempt to hide the origin of that attack. After that, this code was quickly replicated by other cyber criminals, and is believed to be behind the massive attack that brought down the domain registration service provider, Dyn, in October 2016.
How does Mirai malware work?
Mirai uses the Internet things to work. It scans the Internet for IoT (Short for Internet of Things) devices that runs on the ARC processor. Then, this processor runs a stripped-down version of the Linux operating system. In case, the user never changed the default combo-username and password, Mirai is able to log into the device and infect it.
Note: The Mirai botnet employed a hundred thousand hijacked IoT devices to bring down Dyn.
What is the Best Troubleshooter for Ransomware
Ransomware can be in the form of malware, viruses, Trojan, and spread in many other ways, but its agenda is to get the money from the victim. In the very first section, we already discussed few things to perform on daily basis to secure your data, privacy, devices from the catch of hackers. However, sometimes your security tools also may not be able to identify these threats online. So, it’s important that nothing should be one way. You also need to focus and awareness of what’s going on your pc and should have a piece of adequate knowledge about viruses, malware, Trojans, ransomware, and ongoing latest threats so that can judge threats online or offline if your device is compromised.
If you’re already running the antivirus software on your device, then it’s important to check it manually once a day and scan your complete device. You can also set it for default scanning system, depend on some antivirus that may not be developed for default scanning. If you’re antivirus too, or if you haven’t Install the antivirus software, we recommend you to download Waredot Antivirus. It offers the default 3-scan mode that you can choose as per your choice.
It also updates all your outdated software to the latest version. Its HIPS feature makes it best than others alternatives. Its HIPS features keep noticing each activity on the system and do the behavior analysis for suspicious activity. It’s complete pocket-friendly and that’s why it active users crossed-thousand count.
Still, if you’re not up for paid version, try the Waredot Antivirus 30-day free trial and if you feel satisfied, you can go for the paid version, because threats coming all day, and there is no end to it.
Summary
Hey guys! This was the guide about “ransomware 2016.” We’ve listed adequate knowledge for all the ransomware attacks that were held in 2016. We’ve discussed its’ causes, how they spread and how to troubleshoot them. However, you would have seen that treating different ransomware having the same solutions. So, we recommend you that follow the tips we discussed above in the very first section and also use the anti-malware software for better prevention.
Guys, if you think we missed anything crucial thing in this article, we would love to hear from you in the comment box.